SORA SorachanCoin
Shor's algorithm countermeasures / PQC mainnet project

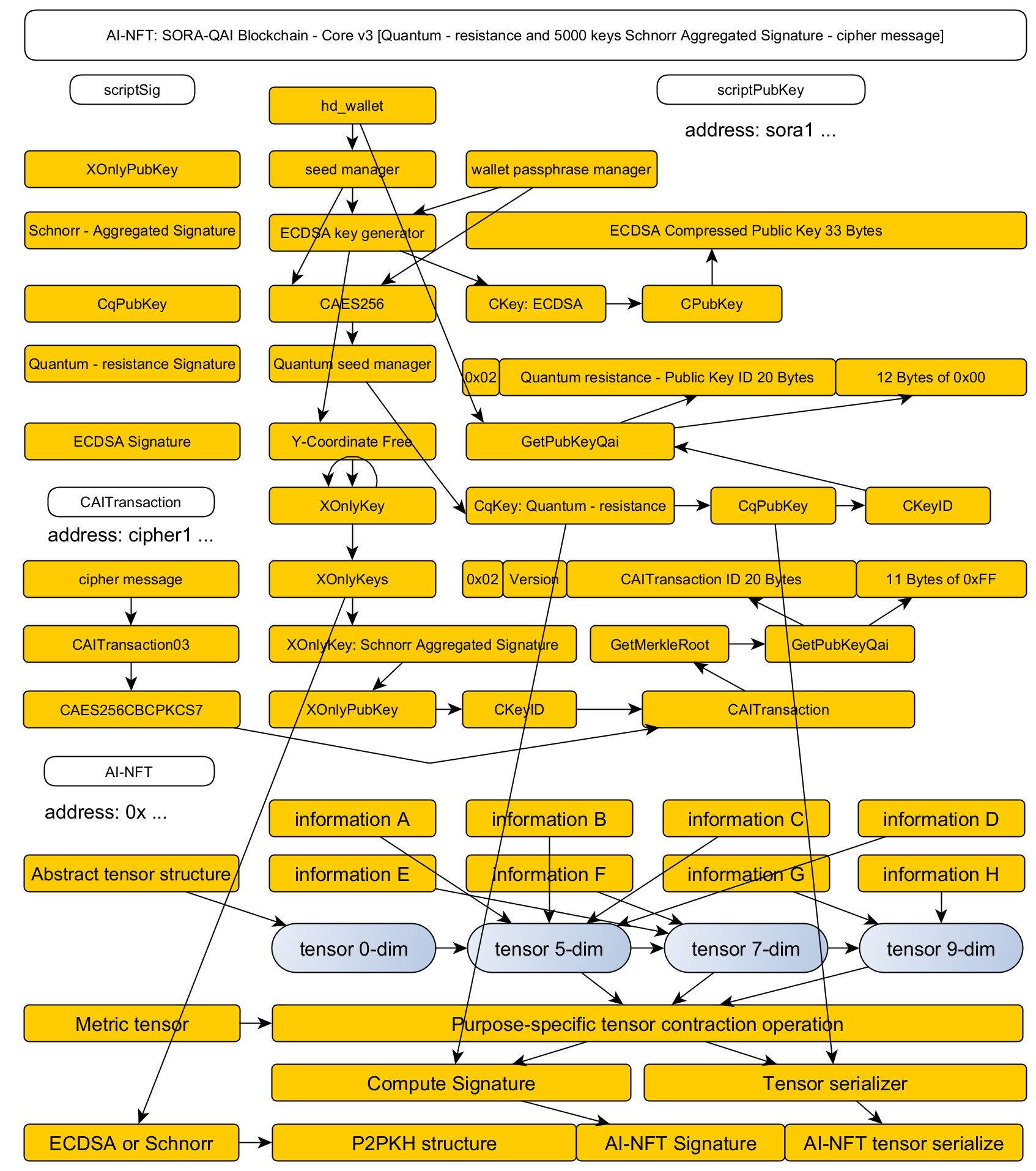
SORA: Shor's algorithm countermeasures / PQC mainnet project
SORA is a project dedicated to implementing and validating post-quantum cryptography (PQC) as a countermeasure against Shor’s algorithm in the quantum domain.
PQC has already been introduced to the mainnet via a soft fork, where it is operating reliably in production. This confirms a crucial point: PQC can be integrated into a blockchain through a soft fork without issue.
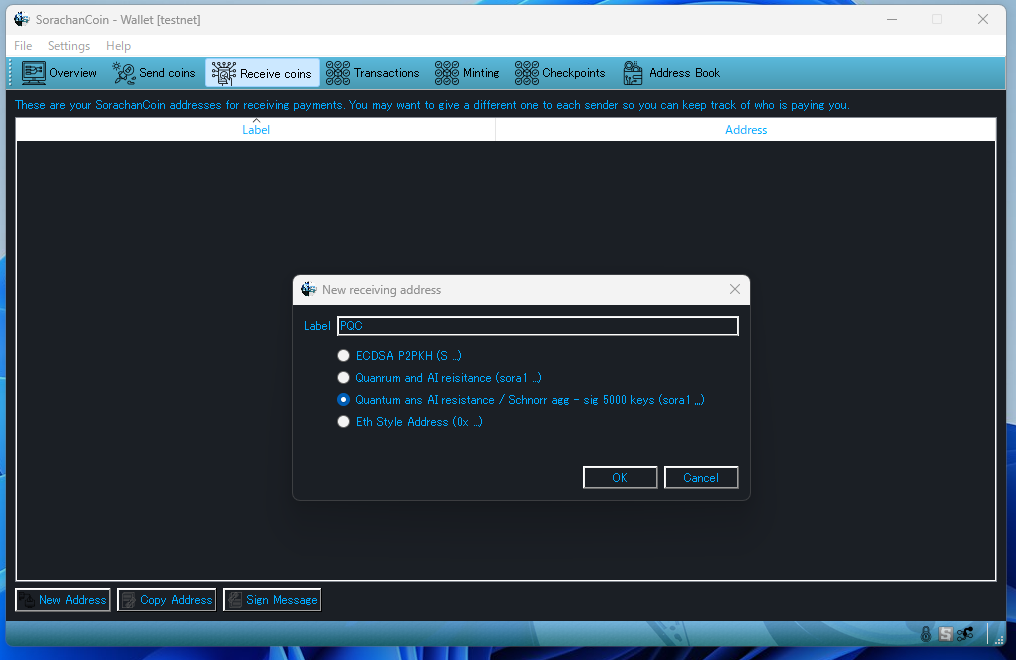
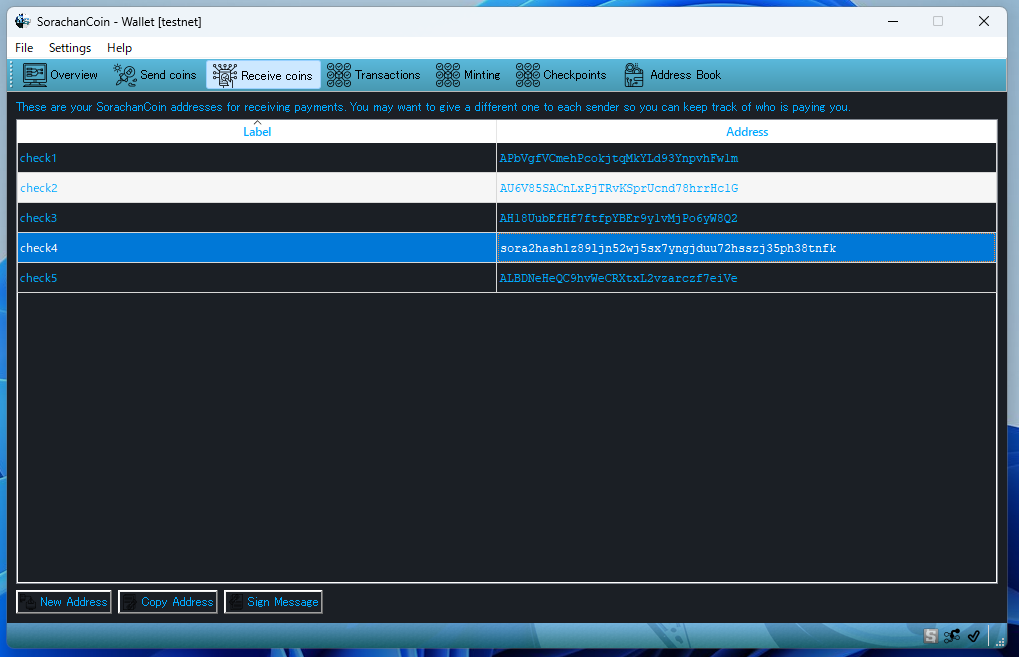
The sora1 address represents the quantum-resistant address format. When coins are sent to this address, they are automatically protected by post-quantum cryptography, providing immediate quantum resistance.